Managing SSO Configurations
Required Privileges
In order to access the Server Options page and configure the Single Sign-On setting, you must have the following:
- Role: User must be assigned to the Role_ocadm.
Configuring SSO
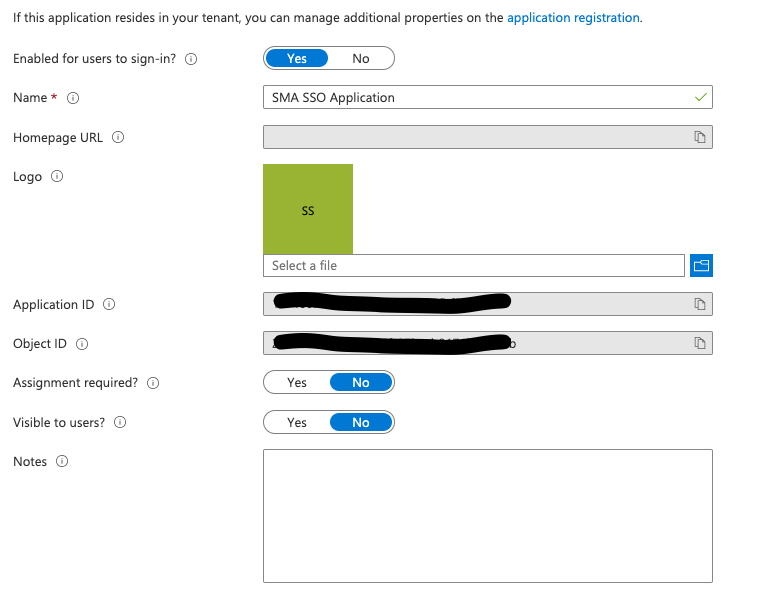
To configure SSO Settings, go to Library > Server Options > click on the SSO panel.
SSO Configuration Fields

Click on the Switch to enable access to the SSO login button.
Enter a Provider. The identity provider (IdP) for the client should be selected from the Provider dropdown. Options include Okta, Azure, and Other.
Enter an Authority. Authority is the URL of the OIDC/OAuth2 provider.
Enter a Client ID. This is your client application's identifier as registered with the OIDC/OAuth2.
Enter a Hostname. The hostname property of the URL interface is a string containing the domain name of the URL. Make sure to include the scheme, which can be HTTP or HTTPS, and the port number, if applicable. For example, https://host:80443.
Enter an Audience. The Audience identifies the recipients that the JWT is intended for.
Enter a Scope. The Scopes being requested from the OIDC/OAuth2 provider (default: "openid"). You can enter various scopes separated by an empty space. For example, openid email.
* OpenID Connect (OIDC) is an open authentication protocol that works on top of the OAuth 2.0 (OAuth2) framework.
Group Mappings
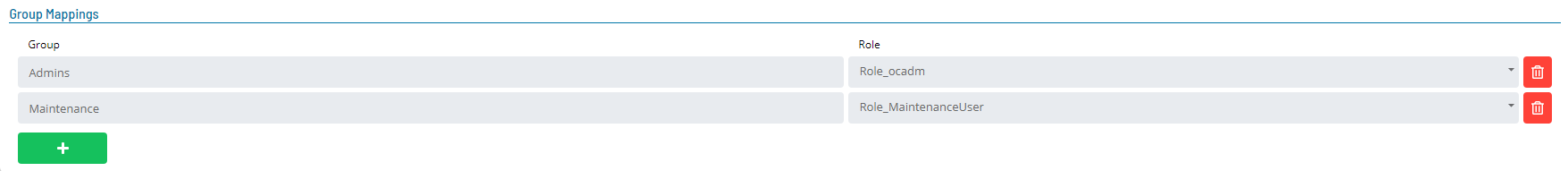
Enter a Group Name: this should match the group name used in your IdP.
Enter a Role: this value represents a valid OpCon role.
Select Save.
- If the switch is in the On position, the user must input values in all fields including values for Group Mappings.
- Examples of how to gather these requirements will be posted below (for the Okta Application and the Azure Application).
- SSO can be implemented with any IdP as long as the required values are provided and they follow the OpenID Connect authentication protocol.
The following are a list of actions that will take place when a user logs in through Single Sign-On.
| Exists in IdP Group | Exists in OpCon | Member of OpCon Role | Can access application in IdP | Enabled in OpCon | Action Taken |
|---|---|---|---|---|---|
| Y | Y | Y | Y | Y | No action user is already in sync |
| Y | N | N/A | Y | N/A | User created and added to role |
| Y | Y | N | Y | Y | User added to role |
| Y | Y | Y | Y | N | User enabled in OpCon |
| Y | Y | Y | N | Y | No action since user cannot access the application |
| Y | Y | Y | N | N | No action since user cannot access the application |
| N | Y | Y | N/A | Y | No action since user does not belong to an existing group |
| N | Y | Y | N/A | N | No action since user does not belong to an existing group |
| N | N | N/A | N/A | N/A | No action |
- Group name values should be unique.
- Group names can be linked to many roles.
- Roles can be linked to many group names.
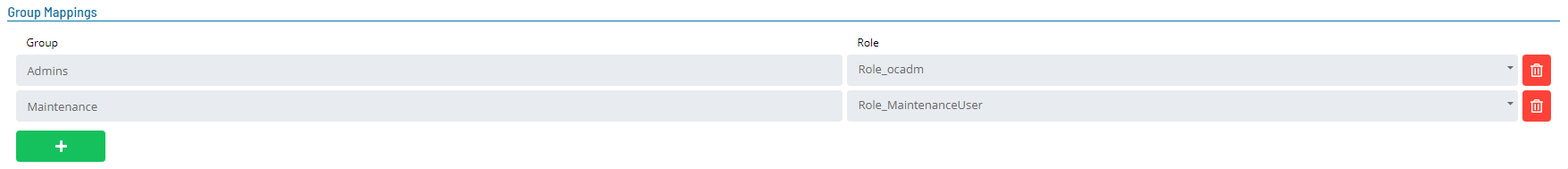
The following is an example of filling out the required fields:
- SSO Settings:

- Group Mappings:
Creating an applications that are OpenID Connect Compatible
Okta Application
This document will describe the steps needed to create a custom application in Okta to return custom optional claims in a access token that will be used by SMAOpConRestApi. Ensure the user following these steps has enough privileges to create an application, assign users to that application, and create custom claims.
- After you’ve logged in to Okta, click "Admin" in the upper right corner to go to the administration dashboard
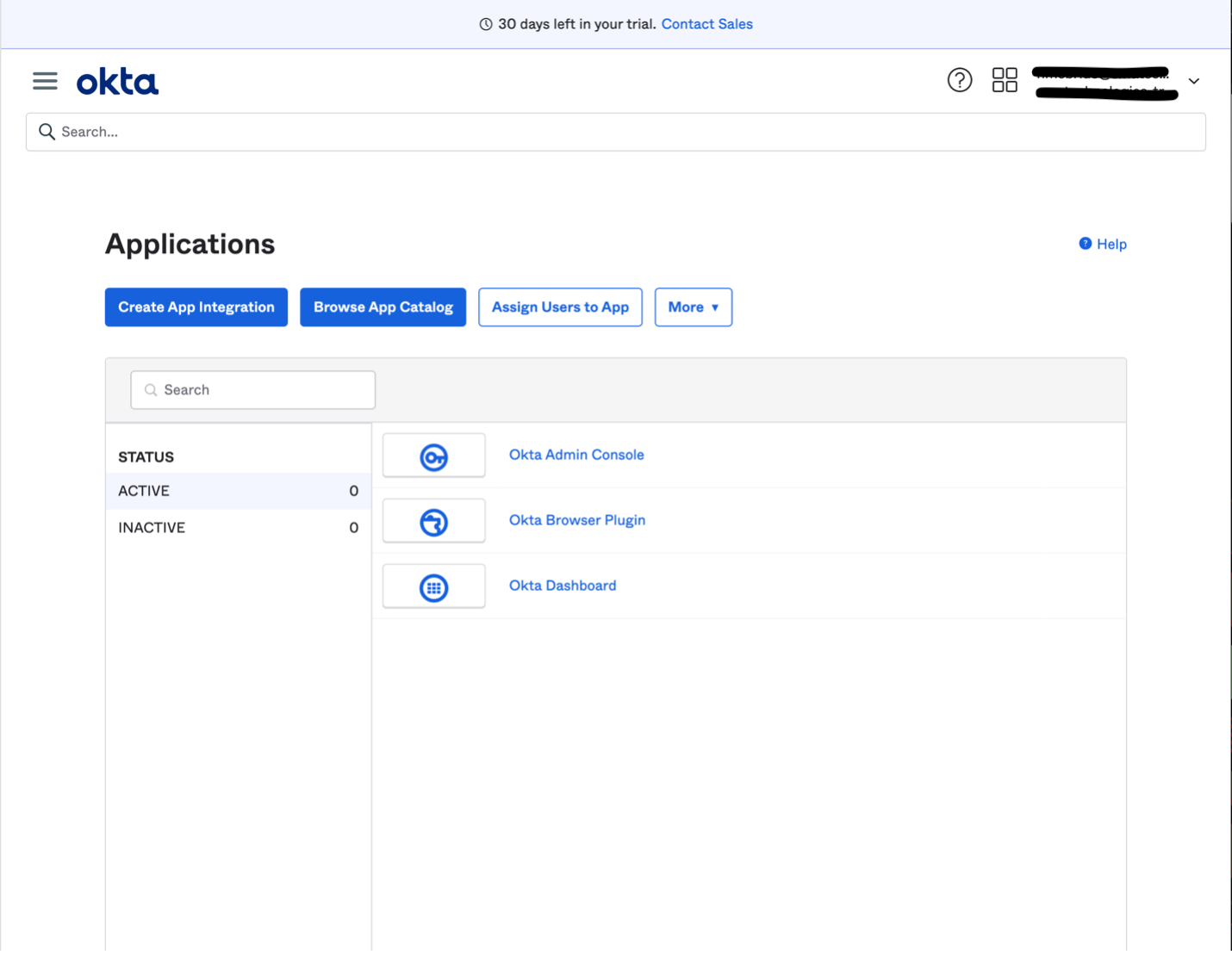
- Once on the administration dashboard, click “Applications” from the left navigation to go to Applications
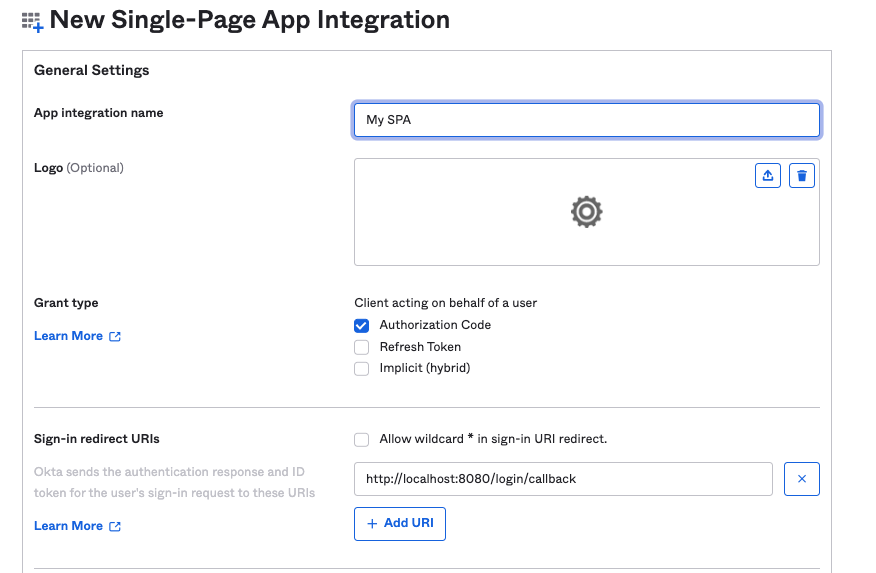
- Click the "Create App Integration" button
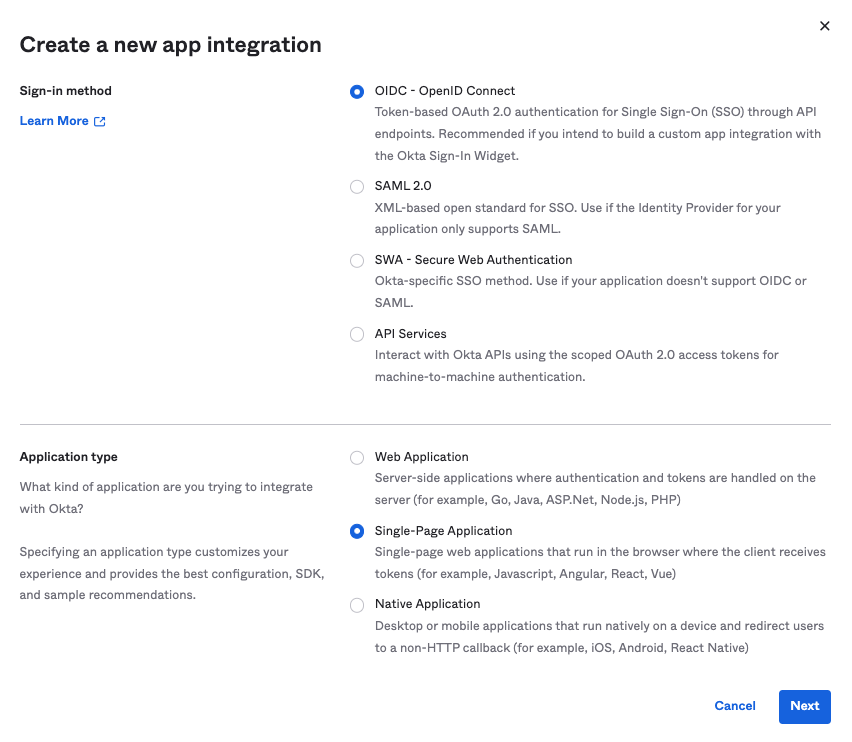
- Inside the modal, select the following options:
- Sign-in method: OIDC - OpenID Connect
- Application type: Single-Page Application
- Click on "Next"
- Set the following options:
- Grant type: Authorization Code
- Sign-in redirects URIs:(sample)
https://<hostname:443>/login/callback- Make sure to include /login/callback
- The hostname will be used on the SSO configuration panel in Solution Manager. Make sure to include the scheme, which can be HTTP or HTTPS, and the port number, if applicable.
- The value for the URL to access Solution Manager will be used in the SSO configuration panel
- Sign-out redirects URIs: This value is not necessary
- Controlled access: Allow everyone in your organization access (for this example)
- If an option was not listed, you may select the one that is more convenient for your organization
- Set controlled access based on your organizations needs
- Click on "Save".
- Note down the Client ID value, this will be used to configure SSO in Solution Manager
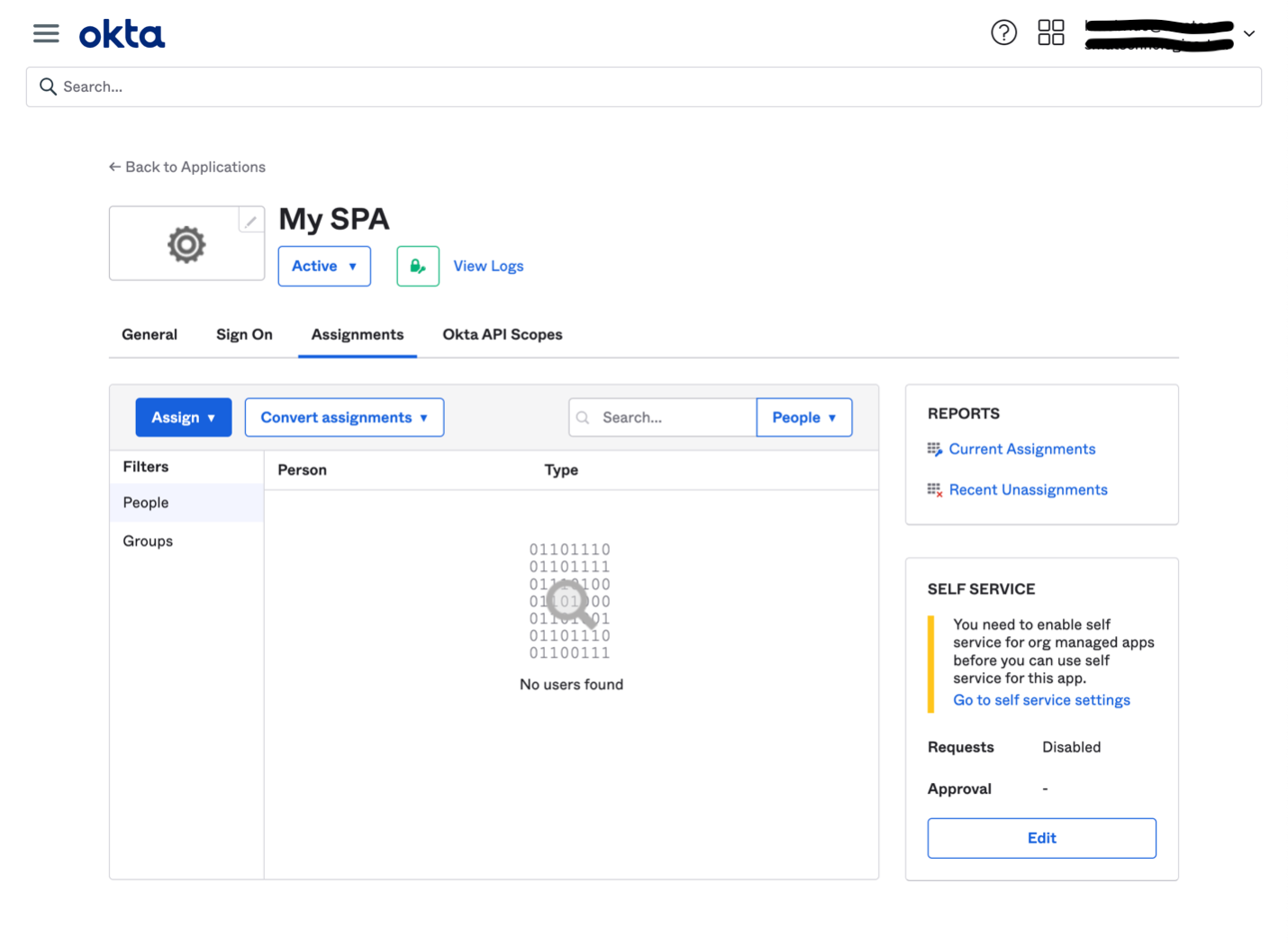
- After creating the application, go the newly created application and go to "Assignments"
- Assign the users from your organization to the new application
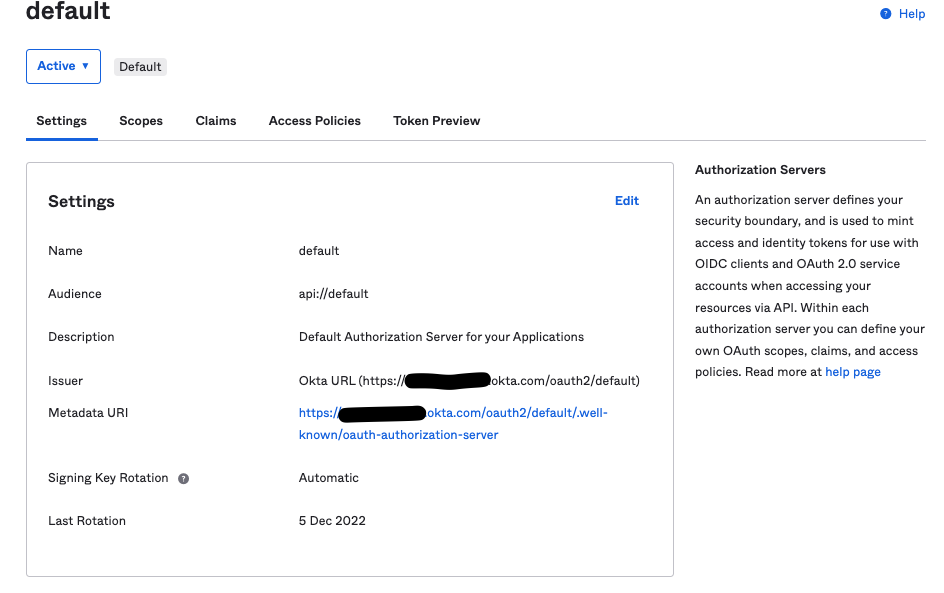
- Go to the "Security" section in the main menu and select "API"
- In the "Authorization Server" tab select the "default" server
- Note down the Issuer URI for the “default” row, this value will be the Authority which will be used in the configuration screen for SSO
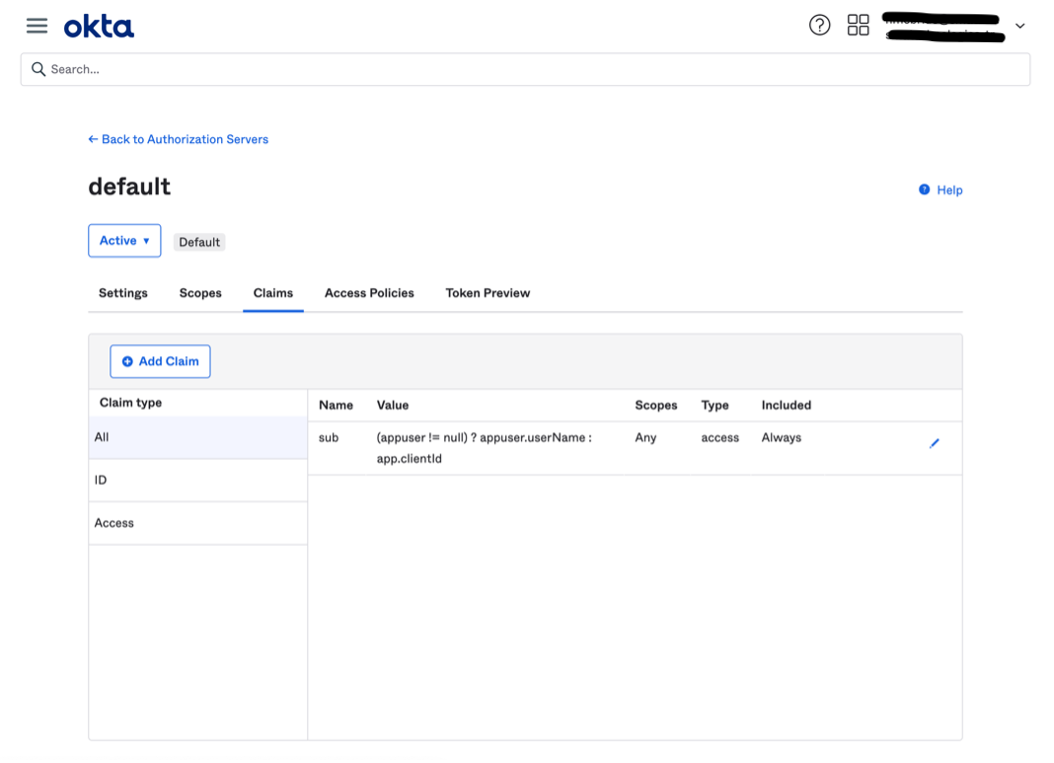
- Inside the "default" authorization server select the "Claims" tab
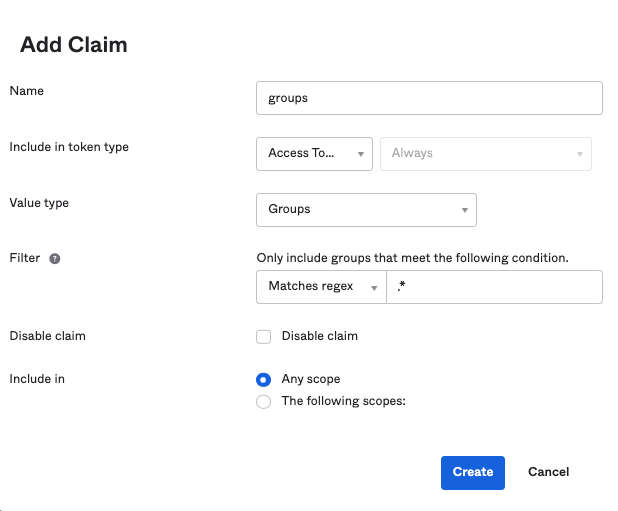
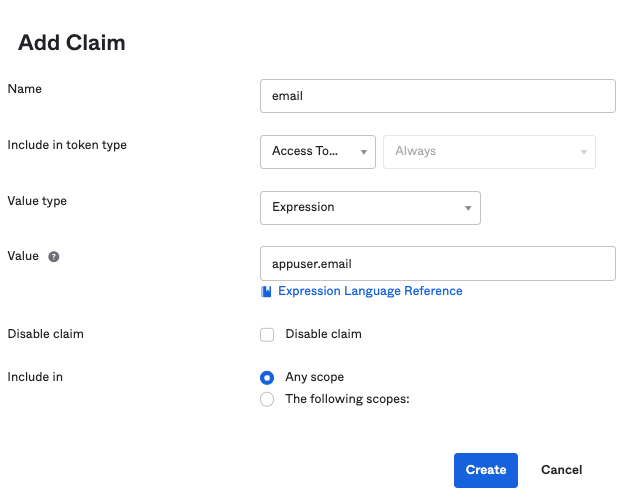
- Click on "Add Claim"
- The following is an example on how to add a custom claim
- Make sure the token type is Access Token and that you enter
.*for the regex logic - Make sure to name claims “groups”
- Repeat the process to add an “email” claim
- Make sure to add appuser.email in the Value text field
- Click on the “Settings” tab and take notes of the following values:
- Audience, this will be used in the SSO configuration panel inside Solution Manager
- Issuer, this will be used as the Authority value in the SSO configuration panel
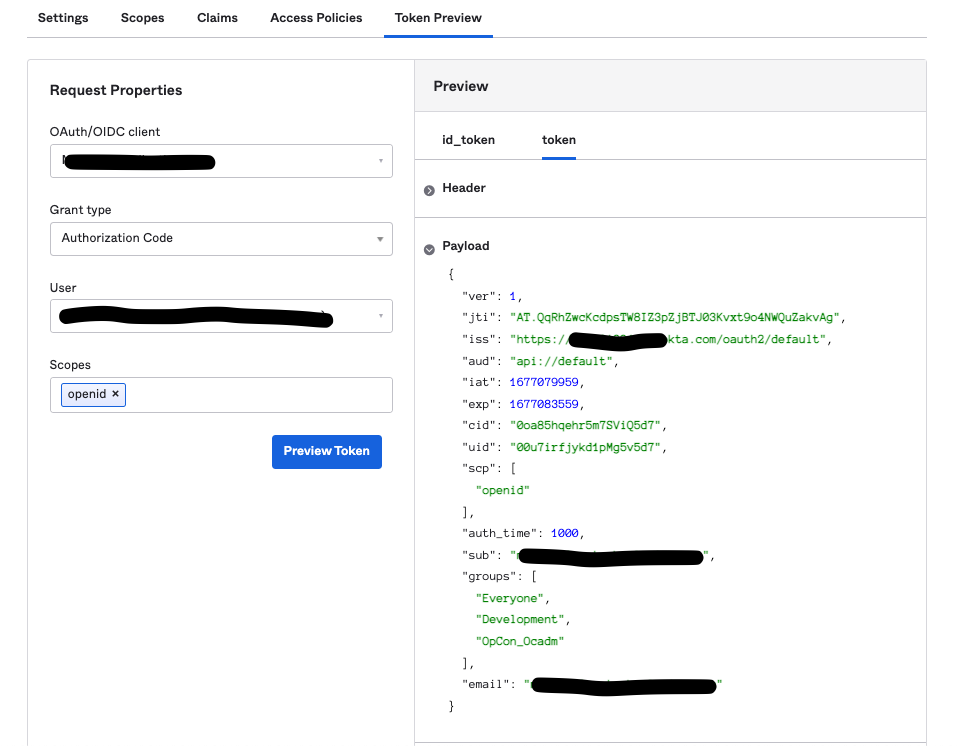
- Go to the "Token Preview" tab
- Type the name your newly created application
- Select Authorization Code for the "Grant Type"
- Select a user that has access to this application
- Type "openid" in the "Scopes" textbox. These scopes are required for SSO implementation in Solution Manager
- Click on "Preview Token" then click on the "token" tab to view the access token. Make sure the “group” and “email” claims are displayed
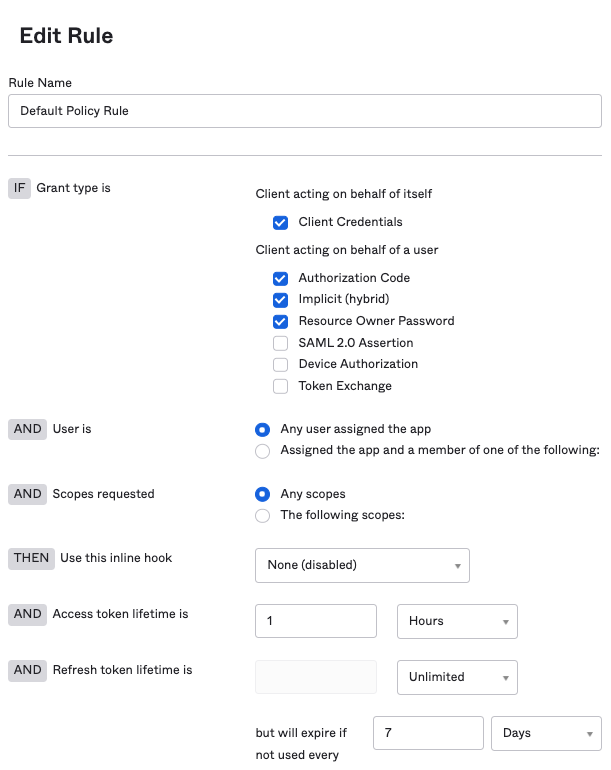
- In the "Authorization Server" tab select the "default" server
- Then click on the "Access Policies" tab
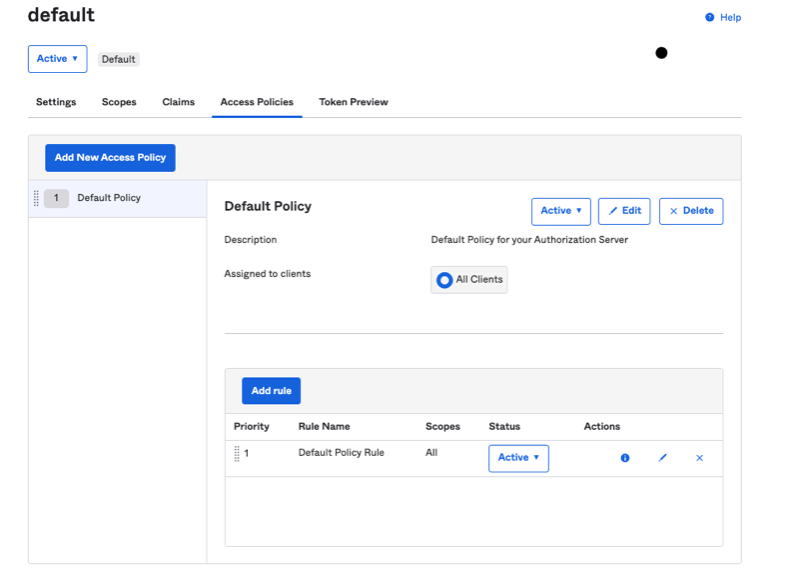
- Click on "Edit" in the "Default Policy Rule" row. Make sure that the "Authorization Code" option is selected, the rest are optional:
- Make sure to the values of “openid“ in the Scope textbox inside the SSO configuration panel inside Solution Manager.
- Make sure the email for the users allowed to access the application matches the username. This value will be used to pair with an existing OpCon user or it will be used to create a new user in the OpCon environment.
Azure Application
This document describes the steps needed to create a custom application in Azure AD that will grant SMAOpConRestApi access to Microsoft Graph API to retrieve user information. Ensure the user following these steps has enough privileges to create an application, assign users to that application, and assign permissions to Microsoft Graph API.
- Go to "Azure Active Directory"
- Go to "App registrations"
- Select new registrations
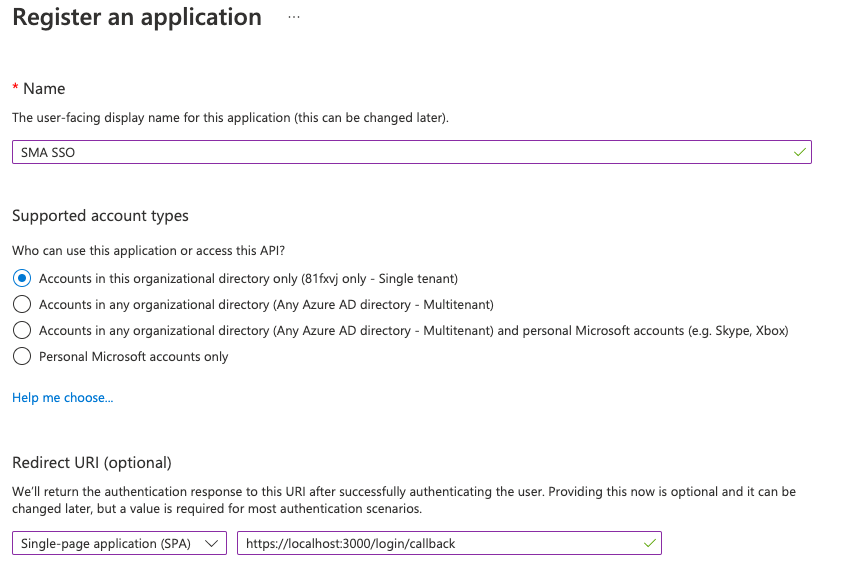
- Add a name to the new application
- Select who can access the application
- For example: Single tenant
- Select Single-page application (SPA)
- Select the redirect URL
- For example,
https://<yourhostname>:8080/login/callback - Make sure to add “/login/callback”
- For example,
- The Hostname used in the redirect URL will be used in the SSO configuration panel inside Solution Manager. Make sure to include the scheme, which can be HTTP or HTTPS, and the port number, if applicable
- Register Application
- Select new registrations
- Select the newly created application
- From the “Home” menu go to Azure Active Directory => App registrations => Select your new application
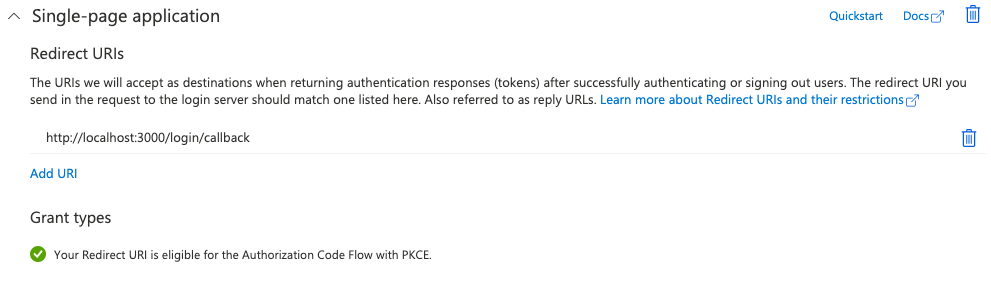
- Go to "Authentication" on the side menu
- Ensure there is a redirect value in the single-page application area. For example,
https://<yourhostname>:8080/login/callback
- Ensure there is a redirect value in the single-page application area. For example,
- Go to “Overview” in the left navigation menu
- Note down the following information, you will need it later:
- The application (client) ID will be used as the Client ID in the SSO configuration panel inside Solution Manager
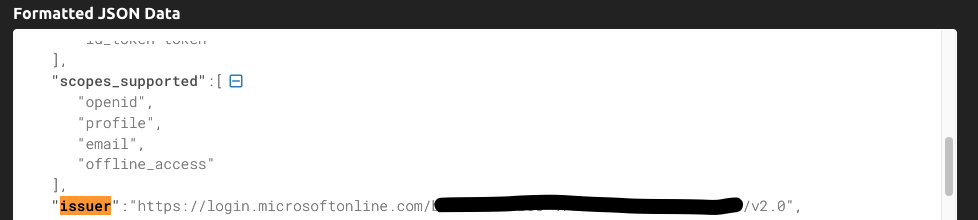
- Click on “Endpoints” and note down the OpenID Connect value
- Copy this value and paste it on a browser and find the issuer value inside the JSON
- It is highly recommended that you copy this text from the browser and paste it into an application that can format the JSON value
- Note down the Issuer URI, this value will be used in the Authority field in the SSO configuration panel inside Solution Manager
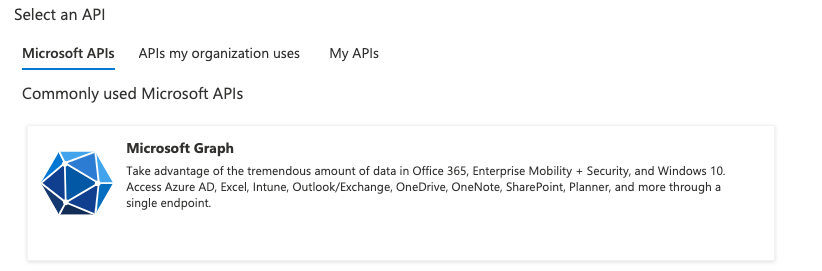
- Go to “API permissions” which is found on the left navigation menu
- Select Add a permission
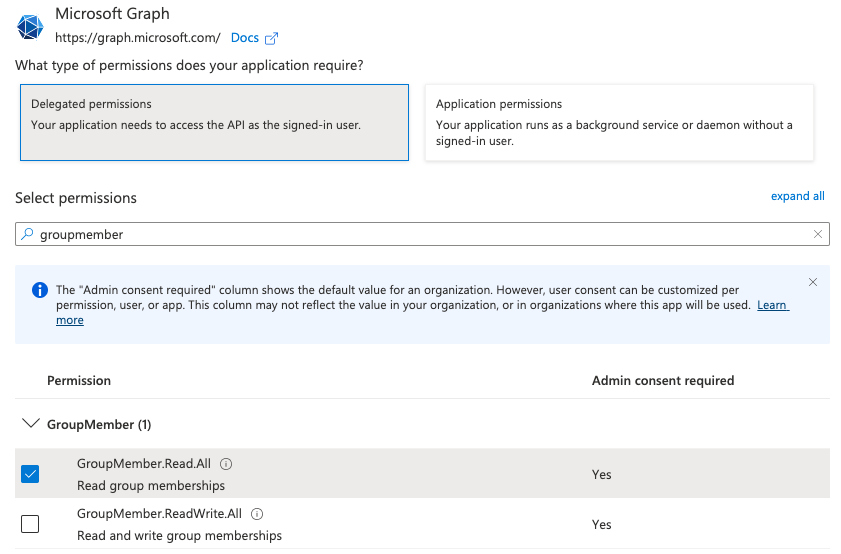
- Click on “Add a permission” and select Microsoft Graph
- Select “Delegated permissions” and type groupmember in the search textbox. Select the GroupMember.Read.All permission:
- Next type user.read in the search textbox and select User.Read permission
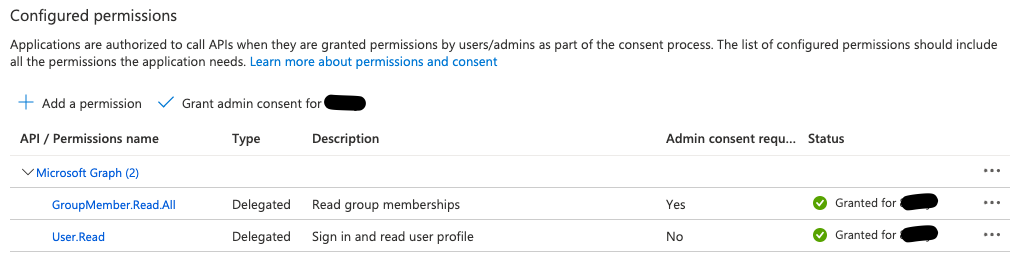
- Click on “Add permissions” to save and then click on “Grant admin consent”
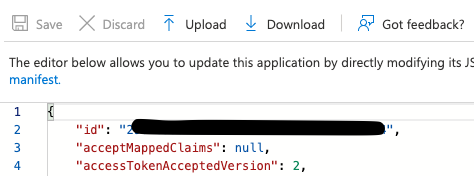
- Go to “Manifest” on the left navigation menu
- Search for “accessTokenAcceptedVersion” and set the value to 2
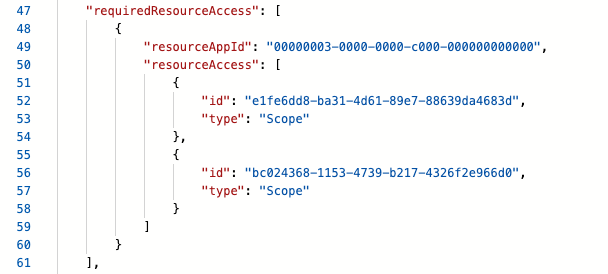
- Then search of the term “resourceAppId” and note down the value. This will be used as the Audience value in the SSO configuration panel in Solution Manager
- Restrict access to the application (optional).
- Go to Azure Active Directory -> Enterprise Applications > All applications and select the application you want to configure
- Select Properties and set "Yes" in the Assignment Required field and save the changes
- Make sure to assign users and groups which need to grant access to the application. Go to Under Manage, select the Users and groups > Add user/group
- Select the users or groups you want to allow and assign them access to your application. Confirm that the users and groups you added are showing up in the updated Users and groups list
- Now only those users/groups are allowed to access to the application
- Make sure to add the “openid” Scope in the SSO configuration panel inside Solution Manager